Contents
I. Introduction

Welcome to the ultimate guide on how to protect your business from cyber threats. In today’s digital age, businesses of all sizes are vulnerable to cyber attacks, which can have devastating consequences. From data breaches to ransomware attacks, the risks are real and the stakes are high.
But fear not! This comprehensive guide will equip you with the knowledge and tools you need to safeguard your business against cyber threats. We’ll cover everything from understanding the different types of cyber threats to implementing effective security measures. Whether you’re a small startup or a large corporation, this guide is tailored to meet your specific needs.
Throughout this guide, we’ll delve into the world of cybersecurity and explore the best practices that can help you stay one step ahead of cybercriminals. We’ll provide practical tips, expert advice, and real-life examples to illustrate the importance of protecting your business from cyber threats.
So, who is this guide for? This guide is for business owners, IT professionals, and anyone who wants to understand the threats posed by cybercriminals and learn how to mitigate those risks. It’s for those who value the security of their business and want to take proactive steps to protect it.
By the end of this guide, you’ll have a solid understanding of the cybersecurity landscape and the steps you need to take to safeguard your business. So, let’s dive in and start building a strong defense against cyber threats!
II. Understanding Cyber Threats

A. Types of cyber threats
When it comes to protecting your business from cyber threats, it’s important to understand the different types of attacks that can occur. By familiarizing yourself with these threats, you can better prepare your business and implement effective security measures. Here are four common types of cyber threats:
- Malware attacks: Malware, short for malicious software, refers to any software designed to harm or exploit computer systems. This can include viruses, worms, Trojans, ransomware, and spyware. Malware attacks can lead to data breaches, system crashes, and unauthorized access to sensitive information.
- Phishing attacks: Phishing attacks involve the use of deceptive emails, messages, or websites to trick individuals into revealing sensitive information such as passwords, credit card details, or social security numbers. These attacks often appear to come from reputable sources and can be highly convincing.
- Denial of Service (DoS) attacks: DoS attacks aim to disrupt the normal functioning of a network, website, or service by overwhelming it with a flood of traffic. This can result in the target becoming inaccessible to legitimate users, causing significant downtime and financial losses.
- Ransomware attacks: Ransomware attacks involve the encryption of a victim’s files or systems, rendering them inaccessible until a ransom is paid. This type of attack can have severe consequences for businesses, as it can lead to data loss, operational disruptions, and financial damages.
B. Common vulnerabilities targeted by cyber threats
In order to effectively protect your business from cyber threats, it’s crucial to be aware of the common vulnerabilities that attackers often exploit. By addressing these vulnerabilities, you can significantly reduce the risk of a successful cyber attack. Here are three common vulnerabilities targeted by cyber threats:
- Weak passwords: Weak passwords are one of the easiest ways for attackers to gain unauthorized access to systems or accounts. Many individuals still use simple and easily guessable passwords, such as “123456” or “password.” It’s important to enforce strong password policies and educate employees about the importance of using unique, complex passwords.
- Outdated software: Outdated software, including operating systems, applications, and plugins, often contain known vulnerabilities that can be exploited by cyber attackers. Regularly updating and patching software is essential to ensure that your systems are protected against the latest threats.
- Lack of employee awareness: Employees can unknowingly become a weak link in your organization’s cybersecurity defenses. Phishing attacks, for example, often rely on employees clicking on malicious links or providing sensitive information. Training employees on cybersecurity best practices and raising awareness about common threats can significantly reduce the risk of successful attacks.
By understanding the different types of cyber threats and the vulnerabilities they exploit, you can take proactive steps to protect your business. Implementing strong security measures, educating employees, and staying up to date with the latest cybersecurity practices are essential in today’s digital landscape.
III. Assessing Your Business’s Vulnerabilities

In order to effectively protect your business from cyber threats, it is crucial to assess your vulnerabilities and understand the potential risks you may face. By conducting a thorough risk assessment and analyzing the consequences of cyber threats, you can develop a comprehensive cybersecurity strategy that addresses your specific needs. In this section, we will explore the key steps involved in assessing your business’s vulnerabilities.
A. Conducting a risk assessment
1. Identifying potential entry points
When conducting a risk assessment, it is important to identify the potential entry points that cybercriminals may exploit to gain unauthorized access to your systems and data. This includes both external and internal entry points. External entry points can include your website, network infrastructure, and remote access systems, while internal entry points can include employee workstations, servers, and other devices connected to your internal network.
By identifying these entry points, you can prioritize your security efforts and implement appropriate measures to protect them. For example, you may choose to implement firewalls, intrusion detection systems, and strong access controls to secure your external entry points, while also implementing endpoint protection solutions and employee training programs to mitigate the risk of internal entry points being compromised.
2. Evaluating existing security measures
Once you have identified the potential entry points, it is important to evaluate the effectiveness of your existing security measures. This involves assessing the strength of your current security controls, such as firewalls, antivirus software, and encryption protocols, and identifying any vulnerabilities or gaps that may exist.
During this evaluation, it is important to consider both technical and non-technical aspects of your security measures. For example, you may assess the effectiveness of your technical controls by conducting vulnerability scans and penetration tests, while also evaluating the adequacy of your security policies, procedures, and employee awareness programs.
By evaluating your existing security measures, you can identify areas for improvement and implement necessary changes to enhance your overall cybersecurity posture.
B. Analyzing potential consequences of cyber threats
1. Financial losses
One of the key consequences of cyber threats is the potential for financial losses. Cyberattacks can result in direct financial losses, such as theft of funds or loss of business income, as well as indirect financial losses, such as the cost of remediation, legal fees, and reputational damage.
When analyzing the potential financial consequences of cyber threats, it is important to consider the impact on your business’s revenue, profitability, and cash flow. This can help you prioritize your cybersecurity investments and allocate resources effectively to mitigate the financial risks.
2. Damage to reputation
Cyberattacks can also have a significant impact on your business’s reputation. A data breach or other security incident can erode customer trust and confidence, leading to a loss of customers, negative media coverage, and damage to your brand image.
When analyzing the potential damage to your reputation, it is important to consider the long-term impact on customer loyalty and brand equity. This can help you develop strategies to rebuild trust and restore your reputation in the event of a cyber incident.
3. Legal implications
Lastly, cyber threats can also have legal implications for your business. Depending on the nature of the incident, you may be subject to legal and regulatory requirements, such as data breach notification laws or industry-specific compliance standards.
When analyzing the potential legal implications, it is important to consult with legal experts to ensure compliance with applicable laws and regulations. This can help you minimize the risk of legal penalties and reputational damage resulting from non-compliance.
By analyzing the potential consequences of cyber threats, you can better understand the risks your business faces and develop a proactive approach to cybersecurity.
IV. Implementing Cybersecurity Measures

Protecting your business from cyber threats is of utmost importance in today’s digital age. Implementing effective cybersecurity measures can help safeguard your sensitive data, prevent unauthorized access, and mitigate potential risks. In this section, we will discuss some essential steps you can take to enhance your business’s cybersecurity.
A. Developing a cybersecurity policy
1. Establishing clear guidelines for employees
One of the first steps in implementing cybersecurity measures is to develop a comprehensive cybersecurity policy. This policy should outline the dos and don’ts for employees when it comes to handling sensitive data and using company resources. By establishing clear guidelines, you can ensure that everyone in your organization understands their responsibilities and the potential risks associated with cybersecurity.
2. Regularly updating the policy
Cyber threats are constantly evolving, and new vulnerabilities are discovered regularly. Therefore, it is crucial to regularly update your cybersecurity policy to address emerging threats and incorporate the latest best practices. By staying up to date, you can better protect your business from new and sophisticated cyber attacks.
B. Installing reliable antivirus and anti-malware software
Installing reliable antivirus and anti-malware software is another essential step in protecting your business from cyber threats. These software solutions help detect and remove malicious programs, such as viruses, worms, and spyware, that can compromise your systems and data. It is important to choose reputable software from trusted vendors and keep it updated to ensure maximum effectiveness.
C. Enforcing strong password policies
1. Utilizing password managers
Enforcing strong password policies is crucial in preventing unauthorized access to your business’s systems and accounts. Encourage your employees to use complex passwords that include a combination of uppercase and lowercase letters, numbers, and special characters. To simplify password management, consider implementing password managers, which securely store and generate strong passwords for different accounts.
2. Implementing multi-factor authentication
In addition to strong passwords, implementing multi-factor authentication (MFA) adds an extra layer of security to your business’s accounts. MFA requires users to provide multiple forms of identification, such as a password and a unique verification code sent to their mobile device, before gaining access. This significantly reduces the risk of unauthorized access, even if a password is compromised.
By implementing these cybersecurity measures, you can significantly enhance your business’s security posture and protect it from cyber threats. Remember to regularly review and update your policies and software to stay ahead of evolving threats. With a proactive approach to cybersecurity, you can safeguard your sensitive data, maintain customer trust, and ensure the long-term success of your business.
V. Securing Your Network
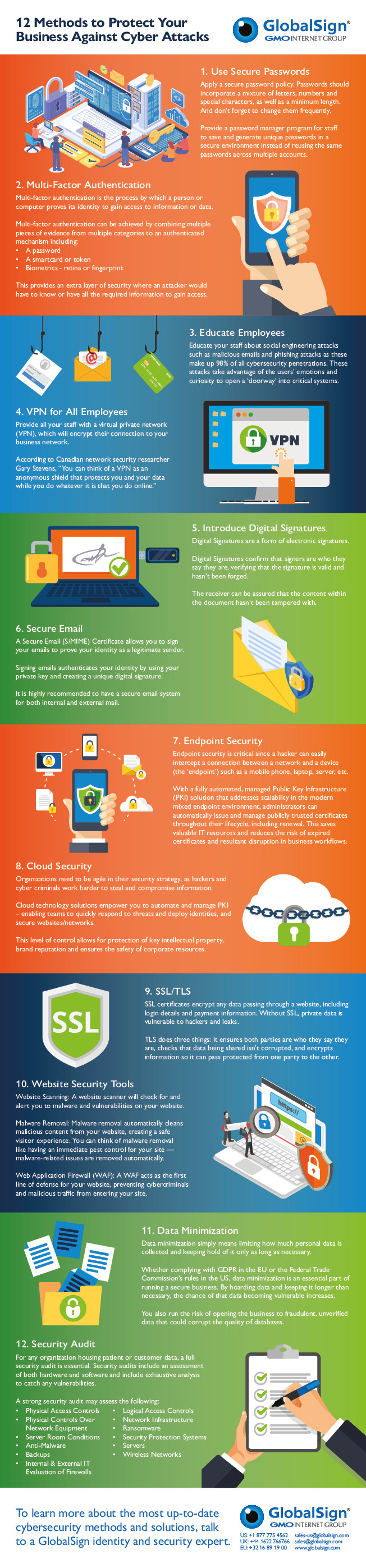
When it comes to protecting your business from cyber threats, securing your network is of utmost importance. In this section, we will explore some key strategies for ensuring the security of your network.
A. Utilizing firewalls and intrusion detection systems
Firewalls and intrusion detection systems (IDS) are essential tools for safeguarding your network against unauthorized access and malicious activities. Firewalls act as a barrier between your internal network and external networks, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. IDS, on the other hand, detect and respond to suspicious activities within your network.
When implementing firewalls and IDS, it’s important to consider the following:
- Choose a reputable firewall and IDS solution that suits your business needs. Look for features such as advanced threat detection, real-time monitoring, and automatic updates.
- Configure your firewall to block unnecessary ports and protocols, allowing only essential traffic to pass through. Regularly review and update your firewall rules to adapt to changing security threats.
- Set up intrusion detection systems to monitor network traffic and identify potential security breaches. Ensure that your IDS is configured to generate alerts and notifications when suspicious activities are detected.
- Regularly update your firewall and IDS software to ensure you have the latest security patches and features. Cybercriminals are constantly evolving their tactics, so staying up to date is crucial.
B. Regularly updating software and firmware
Software and firmware updates play a vital role in maintaining the security of your network. Manufacturers regularly release updates to address vulnerabilities and improve the performance of their products. Failing to update your software and firmware can leave your network exposed to known security risks.
Here are some best practices for software and firmware updates:
- Enable automatic updates whenever possible. This ensures that your devices and applications receive the latest security patches without manual intervention.
- Regularly check for updates manually if automatic updates are not available. Visit the manufacturer’s website or use their software update tools to download and install the latest versions.
- Prioritize critical security updates. Some updates may include new features or bug fixes, but it’s crucial to focus on security-related updates to protect your network.
- Test updates in a controlled environment before deploying them across your entire network. This helps identify any compatibility issues or conflicts that may arise.
C. Implementing secure Wi-Fi networks
Wi-Fi networks are a common entry point for cyber attacks, making it essential to implement secure Wi-Fi practices to protect your network. Here are some steps you can take:
- Change default Wi-Fi network names (SSIDs) and passwords. Default settings are widely known and can make it easier for attackers to gain unauthorized access to your network.
- Use strong encryption protocols such as WPA2 or WPA3. These protocols provide a higher level of security compared to older encryption methods.
- Regularly update your Wi-Fi router’s firmware to ensure it has the latest security patches. Refer to the manufacturer’s instructions for the update process.
- Enable network segmentation to separate guest networks from your internal network. This prevents unauthorized access to sensitive data.
- Implement strong passwords for your Wi-Fi network. Use a combination of uppercase and lowercase letters, numbers, and special characters.
By following these practices, you can significantly enhance the security of your network and protect your business from cyber threats.
VI. Educating Your Employees
When it comes to protecting your business from cyber threats, one of the most crucial steps you can take is to educate your employees. Cybersecurity training sessions are an effective way to ensure that your employees are equipped with the knowledge and skills to identify and prevent potential threats. These sessions should cover a wide range of topics, including the basics of cybersecurity, common types of attacks, and best practices for maintaining a secure work environment.
During these training sessions, it is important to engage your employees and make the content relatable to their everyday work lives. Use real-life examples and case studies to illustrate the potential consequences of cyber attacks and emphasize the importance of following security protocols. Encourage active participation by allowing employees to ask questions and share their own experiences.
In addition to conducting training sessions, raising awareness about phishing attacks is another crucial aspect of educating your employees. Phishing attacks are one of the most common and effective methods used by cybercriminals to gain unauthorized access to sensitive information. By teaching your employees how to recognize and report phishing attempts, you can significantly reduce the risk of falling victim to these attacks.
Provide your employees with practical tips on how to identify phishing emails, such as checking for spelling and grammar errors, verifying the sender’s email address, and avoiding clicking on suspicious links or downloading attachments from unknown sources. Encourage them to report any suspicious emails or activities to the IT department immediately.
Lastly, fostering a culture of reporting suspicious activities is essential for maintaining a strong cybersecurity posture. Employees should feel comfortable reporting any unusual or suspicious behavior they observe, even if they are unsure whether it is a potential threat. This can help your IT team identify and respond to potential threats in a timely manner.
Make sure to establish clear reporting channels and provide employees with the necessary tools and resources to report suspicious activities. Emphasize that reporting such incidents is not only encouraged but also crucial for the overall security of the organization.
VII. Backing Up Data
As a business owner, you understand the importance of protecting your valuable data from cyber threats. One of the most effective ways to safeguard your data is by regularly backing it up. In this section, we will explore the significance of regular data backups, the utilization of cloud storage services, and the implementation of offline backups.
A. Importance of Regular Data Backups
Regular data backups are crucial for the security and continuity of your business. By backing up your data on a regular basis, you ensure that even if your systems are compromised, you can restore your information and resume operations quickly. Here are some key reasons why regular data backups are essential:
- Data Loss Prevention: Accidental deletion, hardware failure, or cyberattacks can lead to data loss. Regular backups provide a safety net, allowing you to recover lost data.
- Business Continuity: In the event of a disaster or system failure, having recent backups ensures that your business can continue functioning with minimal downtime.
- Protection Against Ransomware: Ransomware attacks can encrypt your data and hold it hostage. With regular backups, you can restore your data without paying the ransom.
- Compliance Requirements: Many industries have specific data retention and backup requirements. Regular backups help you meet these compliance standards.
By prioritizing regular data backups, you can minimize the impact of data loss and maintain the integrity of your business.
B. Utilizing Cloud Storage Services
Cloud storage services offer a convenient and secure way to back up your data. These services store your data on remote servers, accessible through the internet. Here are some advantages of utilizing cloud storage services for data backups:
- Automatic Backups: Cloud storage services often provide automated backup solutions, eliminating the need for manual backups.
- Scalability: Cloud storage allows you to easily scale your storage capacity as your business grows, ensuring you have enough space for your backups.
- Remote Access: With cloud storage, you can access your backed-up data from anywhere with an internet connection, providing flexibility and convenience.
- Data Security: Reputable cloud storage providers employ robust security measures, including encryption and regular data backups, to protect your information.
When choosing a cloud storage service, consider factors such as data encryption, reliability, and pricing to find the best fit for your business.
C. Implementing Offline Backups
In addition to cloud storage, implementing offline backups is another important aspect of data protection. Offline backups involve physically storing your data on external devices that are disconnected from the network. Here are some offline backup methods to consider:
- External Hard Drives: External hard drives provide a cost-effective solution for offline backups. Regularly transfer your data to these drives and store them in a secure location.
- Network-Attached Storage (NAS): NAS devices allow you to create your own private cloud storage, providing both local and remote access to your backups.
- Tape Drives: Tape drives offer high-capacity storage and long-term data retention. They are commonly used for archiving purposes and provide an additional layer of protection.
By implementing offline backups, you add an extra layer of security to your data, protecting it from online threats and ensuring its availability even in the absence of internet connectivity.
Remember, backing up your data is not a one-time task. It should be performed regularly to ensure that your backups are up to date and reflect any changes or updates in your business operations. By combining cloud storage services with offline backups, you can create a comprehensive data backup strategy that safeguards your business from cyber threats.
VIII. Monitoring and Detecting Cyber Threats
In today’s digital landscape, businesses are constantly at risk of cyber threats. From data breaches to malware attacks, the consequences of a cyber attack can be devastating. That’s why it’s crucial for businesses to have robust security measures in place to monitor and detect any potential threats. In this section, we will explore the various tools and strategies that businesses can utilize to enhance their security posture.
A. Utilizing security monitoring tools
One of the first steps in protecting your business from cyber threats is to implement security monitoring tools. These tools are designed to continuously monitor your network and systems for any suspicious activities or anomalies. By analyzing network traffic, log files, and system events, these tools can detect potential threats in real-time.
There are several types of security monitoring tools available in the market, each with its own unique features and capabilities. Some tools focus on network monitoring, while others specialize in log file analysis or endpoint detection. It’s important to choose a tool that aligns with your business needs and provides comprehensive coverage.
When selecting a security monitoring tool, consider the following factors:
- Scalability: Ensure that the tool can handle the volume of data generated by your business.
- Real-time alerts: Look for a tool that can send immediate alerts when suspicious activities are detected.
- Integration: Check if the tool can integrate with your existing security infrastructure.
- User-friendly interface: Opt for a tool that is easy to use and provides clear visibility into your network.
By utilizing security monitoring tools, businesses can proactively identify and respond to potential cyber threats, minimizing the impact on their operations and data.
B. Implementing intrusion detection systems
Intrusion detection systems (IDS) are another essential component of a comprehensive cybersecurity strategy. These systems are designed to monitor network traffic and identify any unauthorized access or malicious activities. By analyzing network packets and comparing them against predefined rules and signatures, IDS can detect and alert businesses about potential intrusions.
There are two main types of intrusion detection systems:
- Network-based IDS (NIDS): These systems monitor network traffic and analyze packets to detect any suspicious activities. NIDS can be deployed at strategic points within the network to provide comprehensive coverage.
- Host-based IDS (HIDS): These systems are installed on individual hosts or endpoints to monitor activities at the host level. HIDS can detect unauthorized access attempts, malware infections, and other host-based threats.
When implementing an intrusion detection system, businesses should consider the following:
- Placement: Determine the optimal locations to deploy the IDS sensors for maximum coverage.
- Configuration: Fine-tune the IDS rules and signatures to align with your business requirements.
- Integration: Ensure that the IDS integrates with your existing security infrastructure, such as firewalls and SIEM systems.
- Regular updates: Keep the IDS software and signatures up to date to detect the latest threats.
By implementing intrusion detection systems, businesses can detect and respond to potential intrusions in a timely manner, preventing unauthorized access and data breaches.
C. Conducting regular security audits
Regular security audits are essential to assess the effectiveness of your cybersecurity measures and identify any vulnerabilities or weaknesses. These audits involve a comprehensive review of your systems, processes, and policies to ensure compliance with industry standards and best practices.
During a security audit, businesses should consider the following:
- Network infrastructure: Assess the security of your network devices, such as routers, switches, and firewalls.
- Access controls: Review the access controls in place to ensure that only authorized personnel have access to sensitive data and systems.
- Security policies: Evaluate your security policies and procedures to ensure they are up to date and aligned with industry standards.
- Employee training: Assess the effectiveness of your employee training programs to ensure that employees are aware of cybersecurity best practices.
By conducting regular security audits, businesses can identify and address any vulnerabilities or gaps in their cybersecurity defenses. This proactive approach can help prevent potential cyber threats and minimize the risk of data breaches.
IX. Responding to Cyber Attacks
In today’s digital landscape, businesses face a constant threat from cyber attacks. These attacks can have devastating consequences, ranging from financial loss to reputational damage. As a business owner, it is crucial to have a robust incident response plan in place to effectively deal with such attacks. In this section, we will explore the key steps involved in responding to cyber attacks and protecting your business.
A. Developing an incident response plan
When it comes to dealing with cyber attacks, preparation is key. Developing a comprehensive incident response plan is the first step towards effectively responding to such incidents. This plan should outline the roles and responsibilities of each team member involved in the response process.
Start by identifying the potential threats your business may face and the potential impact they could have. This will help you prioritize your response efforts and allocate resources accordingly. Next, establish a clear chain of command and define the communication channels that will be used during an incident.
It is also important to conduct regular training and drills to ensure that your team is well-prepared to handle cyber attacks. This will help identify any gaps in your incident response plan and allow you to make necessary adjustments.
B. Isolating affected systems
Once a cyber attack has been detected, it is crucial to isolate the affected systems to prevent further damage. This involves disconnecting the compromised systems from the network to contain the attack and minimize its impact.
Start by identifying the source of the attack and determining the extent of the compromise. This will help you understand which systems need to be isolated. Disconnect the affected systems from the network and disable any remote access to prevent the attacker from gaining further control.
During this process, it is important to preserve any evidence that may be needed for forensic analysis. This will help in identifying the attacker and building a case for legal action, if necessary.
C. Engaging with cybersecurity experts
Responding to a cyber attack can be a complex and challenging task. Engaging with cybersecurity experts can provide valuable insights and guidance throughout the process. These experts have the knowledge and experience to help you navigate through the incident and mitigate its impact.
When selecting a cybersecurity expert, look for someone with a proven track record in incident response and a deep understanding of the latest threats and attack techniques. They should be able to assess the situation, provide recommendations for remediation, and assist in the recovery process.
Collaborating with cybersecurity experts can also help you strengthen your overall security posture. They can conduct a thorough assessment of your systems and identify any vulnerabilities that may have been exploited during the attack. By addressing these vulnerabilities, you can reduce the risk of future incidents and better protect your business.
