Contents
- I. Introduction
- II. Historical Context of National Security Threats
- III. Current National Security Threat Landscape
- IV. Cybersecurity Threats
- V. Terrorism as a National Security Threat
- VI. Nuclear Proliferation and Weapons of Mass Destruction
- VII. Economic Espionage and Intellectual Property Theft
- VIII. Border Security and Immigration
- IX. Insider Threats
- A. Definition and Examples of Insider Threats
- B. Analysis of Vulnerabilities within Organizations
- C. Measures to Mitigate Insider Threats
- A. Overview of Biological Threats
- B. Analysis of Potential Pandemics and Their Impact on National Security
- C. Preparedness and Response Strategies for Biological Threats
I. Introduction
Welcome to the comprehensive guide on understanding the threats to national security. In today’s rapidly changing world, national security has become a top priority for governments around the globe. From cyber attacks to terrorism, it is crucial to have a deep understanding of the various threats that can jeopardize a nation’s safety and stability.
In this article, we will explore the multifaceted nature of national security threats and delve into the intricacies of each category. By the end of this guide, you will have a clear understanding of the different types of threats that nations face and the measures they take to mitigate them.
We will begin by examining the evolving landscape of national security threats in the 21st century. With advancements in technology and the interconnectedness of nations, traditional threats have taken on new forms and dimensions. It is essential to grasp the complexities of these emerging threats to effectively address them.
Next, we will delve into the various categories of national security threats. From terrorism and insurgency to cyber warfare and economic espionage, each category presents unique challenges and requires specific strategies for prevention and response.
Throughout this guide, we will also explore case studies and real-world examples to illustrate the impact of these threats on national security. By analyzing past incidents, we can gain valuable insights into the vulnerabilities that exist and learn from the successes and failures of previous responses.
Finally, we will discuss the collaborative efforts between nations and international organizations to combat national security threats. In an increasingly interconnected world, cooperation and information sharing are crucial in effectively countering these challenges.
So, whether you are a policy-maker, a security professional, or simply an individual interested in understanding the threats that affect our world, this guide will provide you with the knowledge and insights needed to navigate the complex landscape of national security threats.
II. Historical Context of National Security Threats

A. Overview of past national security threats
Throughout history, nations have faced various national security threats that have shaped their policies and actions. These threats can come from internal or external sources and can range from military conflicts to economic crises and ideological challenges. Understanding the historical context of these threats is crucial in developing effective national security policies.
One significant past national security threat was the Cold War, which lasted from the late 1940s to the early 1990s. It was a period of intense geopolitical tension between the United States and the Soviet Union, characterized by the arms race, nuclear proliferation, and proxy wars. The threat of a nuclear war posed a significant risk to global security, and both superpowers engaged in espionage and intelligence operations to gather information and gain an advantage.
Another notable historical national security threat was the rise of terrorism in the late 20th century. The attacks on September 11, 2001, marked a turning point in global security as they demonstrated the vulnerability of even the most powerful nations to asymmetric threats. The subsequent War on Terror led to significant changes in national security policies, including increased surveillance, intelligence sharing, and military interventions.
Furthermore, the proliferation of weapons of mass destruction (WMDs) has been a persistent national security concern. The development and acquisition of nuclear, chemical, and biological weapons by rogue states and non-state actors pose a significant threat to global stability. Efforts to prevent the spread of WMDs and disarmament have been key components of national security strategies.
B. Impact of historical events on national security policies
Historical events have a profound impact on national security policies as they shape governments’ perceptions of threats and inform their strategies and responses. The lessons learned from past national security challenges influence decision-making and the allocation of resources.
For example, the lessons learned from the Cold War have influenced the United States’ approach to national security. The emphasis on deterrence, intelligence gathering, and alliances can be traced back to the strategies developed during the Cold War. The recognition of the need for a strong military and intelligence apparatus to counter potential threats is a direct result of the experiences of that era.
The events of September 11, 2001, had a profound impact on national security policies worldwide. The attacks exposed vulnerabilities in intelligence sharing and prompted governments to enhance their counterterrorism efforts. The creation of new agencies, such as the Department of Homeland Security in the United States, and the implementation of stricter security measures at airports and other critical infrastructure are direct responses to the threat of terrorism.
Similarly, the proliferation of WMDs has led to the development of international treaties and agreements aimed at preventing their spread. The Treaty on the Non-Proliferation of Nuclear Weapons (NPT) and the Chemical Weapons Convention (CWC) are examples of international efforts to curb the proliferation of WMDs. National security policies have been shaped by the need to prevent the acquisition of these weapons by hostile actors.
III. Current National Security Threat Landscape

A. Overview of current global threats
In today’s interconnected world, national security threats have become increasingly complex and diverse. As an expert in the field, I have witnessed the evolution of these threats firsthand and understand the urgency of addressing them effectively.
One of the most significant global threats is terrorism. Extremist groups, such as ISIS and Al-Qaeda, continue to pose a serious risk to national security. Their ability to recruit and radicalize individuals online has made it difficult for authorities to track and prevent potential attacks. The rise of lone wolf attacks has further complicated the fight against terrorism.
Cybersecurity has also emerged as a major concern in recent years. With the increasing reliance on digital infrastructure, nations are vulnerable to cyber attacks that can disrupt critical systems, steal sensitive information, and undermine national security. State-sponsored hacking and cyber espionage have become common tactics employed by hostile nations.
Another pressing global threat is nuclear proliferation. The acquisition of nuclear weapons by rogue states or non-state actors poses a grave danger to international stability. Efforts to prevent the spread of nuclear weapons and ensure the safety of existing stockpiles are crucial for maintaining global security.
Additionally, the rise of hybrid warfare has blurred the lines between traditional and non-traditional threats. State-sponsored disinformation campaigns, economic coercion, and proxy wars have become increasingly prevalent strategies used by nations to exert influence and undermine the security of their adversaries.
It is essential for nations to collaborate and develop comprehensive strategies to address these global threats. International cooperation, intelligence sharing, and investment in cutting-edge technologies are key to effectively combating these challenges.
B. Analysis of emerging threats
As the world continues to evolve, new threats to national security are constantly emerging. It is crucial to stay ahead of these threats and adapt strategies accordingly. Drawing from my expertise and experience, I will analyze some of the most significant emerging threats.
One such threat is the rise of artificial intelligence (AI) and its potential for misuse. While AI has the potential to revolutionize various sectors, including defense and security, it also presents risks. Malicious actors could exploit AI to develop autonomous weapons or sophisticated cyber attack tools, which could have devastating consequences.
The increasing interconnectedness of critical infrastructure through the Internet of Things (IoT) also poses a significant threat. Vulnerabilities in IoT devices can be exploited to disrupt essential services, such as power grids, transportation systems, and communication networks. Ensuring the security of these interconnected systems is paramount.
Climate change is another emerging threat that has far-reaching implications for national security. Rising sea levels, extreme weather events, and resource scarcity can lead to conflicts over land, water, and other vital resources. The destabilizing effects of climate change can exacerbate existing tensions and create new security challenges.
The rapid advancement of biotechnology and genetic engineering raises concerns about the potential misuse of biological agents as weapons. The deliberate release of a deadly pathogen or the creation of genetically modified organisms with harmful properties could have catastrophic consequences.
Lastly, the proliferation of disinformation and fake news poses a significant threat to national security. False narratives and manipulated information can sow discord, undermine trust in democratic institutions, and incite violence. Developing effective strategies to counter disinformation and promote media literacy is crucial in the digital age.
As the national security threat landscape continues to evolve, it is imperative for governments, organizations, and individuals to remain vigilant and proactive. By understanding and addressing these emerging threats, we can safeguard our nations and ensure a secure future for all.
IV. Cybersecurity Threats

In today’s digital age, cybersecurity threats have become a major concern for individuals, businesses, and governments alike. The rapid advancement of technology has brought about new opportunities and conveniences, but it has also opened the door to various types of cyber threats. In this section, we will explore the definition and types of cybersecurity threats, provide examples of high-profile cyber attacks, and discuss the impact of these threats on national security.
A. Definition and Types of Cybersecurity Threats
Cybersecurity threats refer to any malicious activities or actions that aim to compromise the confidentiality, integrity, or availability of computer systems, networks, or data. These threats can come in various forms and can be carried out by individuals, organized groups, or even nation-states.
One of the most common types of cybersecurity threats is malware. Malware, short for malicious software, includes viruses, worms, Trojans, ransomware, and spyware. These malicious programs are designed to infiltrate computer systems, steal sensitive information, disrupt operations, or hold data hostage for financial gain.
Another type of cybersecurity threat is phishing. Phishing attacks involve the use of deceptive emails, messages, or websites to trick individuals into revealing their personal information, such as passwords, credit card numbers, or social security numbers. These attacks often mimic legitimate organizations or individuals, making it difficult for users to distinguish between genuine and fake communications.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks are also common cybersecurity threats. These attacks aim to overwhelm a target system or network with a flood of traffic, rendering it inaccessible to legitimate users. Hackers often use botnets, which are networks of compromised computers, to carry out these attacks.
Other types of cybersecurity threats include insider threats, where individuals within an organization intentionally or unintentionally compromise security, and advanced persistent threats (APTs), which are sophisticated, long-term attacks that target specific organizations or individuals.
B. Examples of High-Profile Cyber Attacks
Over the years, there have been numerous high-profile cyber attacks that have made headlines and highlighted the severity of cybersecurity threats. These attacks have targeted various sectors, including government agencies, financial institutions, healthcare organizations, and multinational corporations.
One notable example is the 2017 WannaCry ransomware attack, which affected hundreds of thousands of computers in over 150 countries. The attack exploited a vulnerability in the Windows operating system and encrypted users’ files, demanding a ransom in Bitcoin for their release. This attack caused widespread disruption and financial losses, highlighting the need for robust cybersecurity measures.
Another significant cyber attack was the 2014 breach of Sony Pictures Entertainment. The attack, attributed to North Korean hackers, resulted in the theft and release of sensitive company data, including confidential emails, employee information, and unreleased films. This attack not only caused financial losses but also had far-reaching implications for the company’s reputation and relationships with business partners.
In 2015, the Office of Personnel Management (OPM) in the United States fell victim to a massive data breach. The attack compromised the personal information of millions of current and former federal employees, including social security numbers, fingerprints, and background investigation records. This breach highlighted the vulnerability of government agencies to cyber attacks and the need for enhanced security measures.
C. Impact of Cyber Threats on National Security
Cyber threats pose a significant risk to national security, as they can target critical infrastructure, government systems, and sensitive information. A successful cyber attack on a nation’s infrastructure, such as power grids, transportation networks, or communication systems, can have devastating consequences and disrupt essential services.
Cyber attacks on government systems can compromise national defense capabilities, intelligence operations, and diplomatic relations. They can also undermine public trust in government institutions and erode confidence in the ability to protect sensitive information.
Furthermore, cyber threats can have economic implications, as they can result in financial losses, intellectual property theft, and disruption of business operations. They can also impact international trade and competitiveness, as companies may hesitate to engage in digital transactions or share sensitive information due to security concerns.
To mitigate the impact of cyber threats on national security, governments around the world are investing in cybersecurity initiatives, strengthening regulations, and fostering international cooperation. It is crucial for individuals, organizations, and governments to remain vigilant, adopt robust cybersecurity measures, and stay informed about emerging threats to safeguard national security in an increasingly interconnected world.
V. Terrorism as a National Security Threat

In today’s world, terrorism has become a major concern for nations across the globe. It poses a significant threat to national security, stability, and peace. In this section, we will delve into the definition and types of terrorism, analyze major terrorist organizations, and explore strategies to counter this menace.
A. Definition and Types of Terrorism
Terrorism can be defined as the use of violence, intimidation, or coercion to achieve political, religious, or ideological objectives. It is a deliberate act aimed at instilling fear, causing harm, and disrupting the normal functioning of society.
There are various types of terrorism, each with its own characteristics and motivations. Some common types include:
- Political Terrorism: This form of terrorism is driven by political ideologies and aims to bring about political change or overthrow existing governments. It often targets government officials, infrastructure, and public spaces.
- Religious Terrorism: Religious terrorism is motivated by religious beliefs and seeks to advance a particular religious agenda. It can involve attacks on religious institutions, religious leaders, or individuals belonging to different religious groups.
- State-Sponsored Terrorism: State-sponsored terrorism refers to acts of terrorism supported or sponsored by a nation-state. It is often used as a tool of foreign policy to exert influence, destabilize other countries, or suppress dissent.
- Cyber Terrorism: With the increasing reliance on technology, cyber terrorism has emerged as a significant threat. It involves the use of computer networks and information systems to carry out attacks, disrupt critical infrastructure, or steal sensitive information.
- Domestic Terrorism: Domestic terrorism occurs within a country and is perpetrated by individuals or groups with grievances against their own government or society. It can be driven by political, ideological, or social factors.
It is important to understand these different types of terrorism as they have distinct characteristics and require tailored approaches to counter them effectively.
B. Analysis of Major Terrorist Organizations
Across the world, there are several major terrorist organizations that pose significant threats to national security. These organizations have global reach, sophisticated networks, and access to resources that enable them to carry out large-scale attacks. Let’s take a closer look at some of these groups:
| Terrorist Organization | Region of Operation | Ideology |
|---|---|---|
| ISIS (Islamic State of Iraq and Syria) | Middle East, North Africa | Salafi-jihadism |
| Al-Qaeda | Global | Salafi-jihadism |
| Taliban | Afghanistan, Pakistan | Islamic fundamentalism |
| Boko Haram | West Africa | Jihadism |
| Hezbollah | Lebanon, Middle East | Shia Islamism |
These organizations have carried out numerous attacks, resulting in loss of lives and widespread destruction. They exploit political, religious, and social grievances to recruit members and propagate their ideologies. Combating these organizations requires a comprehensive and coordinated approach involving intelligence sharing, law enforcement cooperation, and targeted military operations.
C. Strategies to Counter Terrorism
Addressing the threat of terrorism requires a multi-faceted approach that combines preventive measures, intelligence gathering, law enforcement efforts, and international cooperation. Here are some strategies that can be employed to counter terrorism:
- Intelligence Sharing: Effective intelligence sharing between countries is crucial in identifying and disrupting terrorist activities. Timely and accurate information can help prevent attacks and dismantle terrorist networks.
- Law Enforcement Cooperation: Close collaboration between law enforcement agencies at the national and international levels is essential in investigating and apprehending terrorists. This includes sharing resources, expertise, and best practices.
- Border Security: Strengthening border security measures can help prevent the movement of terrorists, weapons, and illicit funds across borders. This includes implementing robust immigration controls, utilizing advanced technology, and enhancing cooperation with neighboring countries.
- Countering Radicalization: Addressing the root causes of radicalization is crucial in preventing individuals from joining terrorist organizations. This involves promoting social inclusion, providing education and economic opportunities, and countering extremist ideologies.
- International Cooperation: Terrorism is a global problem that requires a collective response. International cooperation, through platforms such as the United Nations and regional organizations, is essential in coordinating efforts, sharing information, and implementing joint counter-terrorism initiatives.
It is important to recognize that countering terrorism is a long-term endeavor that requires sustained commitment, resources, and collaboration. By adopting a comprehensive and multi-dimensional approach, nations can effectively mitigate the threat posed by terrorism and safeguard their national security.
VI. Nuclear Proliferation and Weapons of Mass Destruction
In today’s world, the threat of nuclear proliferation and weapons of mass destruction (WMDs) poses a significant challenge to national security. The increasing number of countries with nuclear capabilities and the implications of WMDs on global stability cannot be ignored. In this section, we will provide an overview of nuclear proliferation, analyze countries with nuclear capabilities, and discuss the implications of WMDs on national security.
A. Overview of nuclear proliferation
Nuclear proliferation refers to the spread of nuclear weapons to countries that do not have them. The proliferation of nuclear weapons has been a major concern for the international community due to the potential catastrophic consequences they can cause. The development and possession of nuclear weapons by a country can significantly alter the balance of power and threaten regional and global stability.
The Nuclear Non-Proliferation Treaty (NPT) is an international treaty aimed at preventing the spread of nuclear weapons and promoting disarmament. It has been signed by 191 countries, making it one of the most widely accepted arms control agreements. However, some countries have chosen not to sign the treaty or have withdrawn from it, raising concerns about the effectiveness of non-proliferation efforts.
Despite efforts to prevent nuclear proliferation, several countries have successfully developed nuclear weapons. These countries include the United States, Russia, China, the United Kingdom, France, India, Pakistan, Israel, and North Korea. The possession of nuclear weapons by these countries has created a complex geopolitical landscape and increased the risk of nuclear conflict.
B. Analysis of countries with nuclear capabilities
When analyzing countries with nuclear capabilities, it is essential to consider their motivations, capabilities, and potential risks. The United States and Russia possess the largest nuclear arsenals, with thousands of warheads each. These two countries have historically been engaged in a nuclear arms race, which has shaped global security dynamics.
China, the United Kingdom, France, and India are also recognized nuclear powers. These countries have developed nuclear weapons for various reasons, including deterrence, prestige, and regional security concerns. Pakistan and Israel are widely believed to possess nuclear weapons, although they have not officially declared their capabilities.
North Korea’s nuclear program has been a significant source of concern for the international community. The country has conducted several nuclear tests and missile launches, defying international sanctions and raising tensions in the region. The unpredictable nature of North Korea’s leadership and its aggressive rhetoric have heightened fears of a potential nuclear conflict.
C. Implications of weapons of mass destruction on national security
The implications of weapons of mass destruction (WMDs) on national security are far-reaching. WMDs include not only nuclear weapons but also chemical and biological weapons. The use of these weapons can cause massive casualties, disrupt societies, and have long-lasting environmental and health effects.
One of the main concerns regarding WMDs is the possibility of their acquisition by non-state actors, such as terrorist organizations. The threat of terrorist groups obtaining and using WMDs is a nightmare scenario for national security agencies worldwide. Efforts to prevent the proliferation of WMDs and secure existing stockpiles are crucial in countering this threat.
Additionally, the presence of WMDs can lead to an arms race among countries, as states seek to maintain a balance of power and deter potential adversaries. This arms race can divert significant resources from other areas, such as social welfare and economic development.
The international community has taken various measures to address the threat of WMDs. These measures include arms control agreements, non-proliferation initiatives, and efforts to strengthen international norms against the use of WMDs. However, the challenges posed by WMDs continue to evolve, requiring constant vigilance and cooperation among nations.
VII. Economic Espionage and Intellectual Property Theft
Economic espionage and intellectual property theft are serious threats to national security, with far-reaching implications for both the economy and the country as a whole. In this section, we will explore the definition and examples of economic espionage, the impact of intellectual property theft on national security, and the measures that can be taken to protect against these threats.
A. Definition and Examples of Economic Espionage
Economic espionage refers to the illegal and covert activities undertaken by individuals, organizations, or governments to gather confidential or proprietary information from another entity, typically for economic or competitive advantage. This can include stealing trade secrets, proprietary technology, research and development data, customer lists, and other valuable information.
Examples of economic espionage are numerous and varied. One high-profile case is the hacking of Equifax in 2017, where sensitive personal information of millions of individuals was stolen. This breach not only had severe financial implications for the company but also compromised the personal and financial security of the affected individuals.
Another example is the theft of intellectual property by foreign governments or entities. For instance, Chinese hackers have been accused of stealing valuable trade secrets from American companies in industries such as technology, aerospace, and pharmaceuticals. These stolen intellectual property rights can be used to gain a competitive advantage in the global market, undermining the economic interests of the affected countries.
B. Impact of Intellectual Property Theft on National Security
The theft of intellectual property has significant implications for national security. When valuable trade secrets, proprietary technology, and research data are stolen, it can undermine the competitiveness and innovation of a country’s industries. This can lead to economic losses, job cuts, and a decline in the overall economic well-being of the nation.
Furthermore, intellectual property theft can have serious implications for national defense and security. For example, stolen military technology or research data can be used by foreign adversaries to develop advanced weapons systems or gain insight into a country’s defense capabilities. This compromises national security and can pose a direct threat to the safety and sovereignty of the nation.
Additionally, intellectual property theft can erode trust and confidence in the affected industries, both domestically and internationally. Companies may be hesitant to invest in research and development or share valuable information for fear of it being stolen. This hampers innovation and collaboration, hindering the growth and competitiveness of the affected industries.
C. Measures to Protect Against Economic Espionage
Protecting against economic espionage requires a multi-faceted approach involving various stakeholders, including governments, businesses, and individuals. Here are some measures that can be taken to mitigate the risk:
- 1. Enhancing cybersecurity: Implement robust cybersecurity measures to protect sensitive information from unauthorized access. This includes using strong passwords, encryption, firewalls, and regularly updating security software.
- 2. Employee education and awareness: Train employees on the importance of cybersecurity and the risks associated with economic espionage. Encourage them to follow best practices, such as avoiding suspicious emails or links, and reporting any unusual activities.
- 3. Intellectual property protection: Register patents, trademarks, and copyrights to protect valuable intellectual property. Implement strict access controls and non-disclosure agreements to safeguard trade secrets and proprietary information.
- 4. Collaboration and information sharing: Foster collaboration between government agencies, industry associations, and businesses to share information on emerging threats and best practices. This collective effort can help identify and address vulnerabilities more effectively.
- 5. International cooperation: Strengthen international cooperation and information sharing to combat economic espionage. This includes sharing intelligence, coordinating investigations, and imposing sanctions on countries or entities involved in intellectual property theft.
By implementing these measures, countries can better protect themselves against economic espionage and intellectual property theft, safeguarding their national security and economic interests.
VIII. Border Security and Immigration
Border security plays a crucial role in ensuring national security. It involves the protection of a country’s borders to prevent unauthorized entry and the smuggling of goods, drugs, and weapons. Effective border security measures are essential for maintaining the safety and well-being of a nation and its citizens.
Immigration policies also have a significant impact on national security. The analysis of these policies is essential to understand their implications and potential risks. Immigration can bring both positive and negative effects, and it is crucial to strike a balance that prioritizes national security while also considering humanitarian concerns.
Enhancing border security requires the implementation of various strategies. These strategies aim to strengthen border control and surveillance, improve intelligence gathering and sharing, and enhance cooperation with international partners. By adopting a multi-faceted approach, countries can effectively address the challenges posed by border security and immigration.
A. Importance of border security for national security
Border security is of paramount importance for national security. It serves as the first line of defense against threats such as terrorism, organized crime, and illegal activities. By effectively securing borders, countries can prevent the entry of individuals who may pose a risk to national security.
One of the primary objectives of border security is to prevent the unauthorized entry of individuals. This includes individuals with criminal backgrounds, potential terrorists, and those involved in human trafficking or drug smuggling. By implementing robust border control measures, countries can significantly reduce the risk of such individuals entering their territory.
Border security also plays a crucial role in protecting a country’s economy. It helps prevent the smuggling of goods, counterfeit products, and illegal drugs, which can have a detrimental impact on local industries and public health. By ensuring the integrity of borders, countries can safeguard their economic interests and promote fair trade.
Furthermore, border security contributes to the overall stability and social cohesion of a nation. By effectively managing immigration and preventing the entry of unauthorized individuals, countries can maintain social harmony and reduce the potential for conflicts arising from cultural, religious, or economic differences.
B. Analysis of immigration policies and their impact on national security
Immigration policies have a significant impact on national security. These policies determine who can enter a country, under what conditions, and for what purposes. It is essential to analyze these policies to assess their effectiveness in addressing national security concerns.
One aspect of immigration policies that impacts national security is the screening and vetting process for individuals seeking entry. Robust screening procedures help identify potential risks and ensure that only individuals who meet the necessary criteria are granted entry. By implementing thorough background checks and intelligence sharing, countries can mitigate security threats.
Another consideration is the management of refugee and asylum-seeker flows. While it is essential to provide humanitarian assistance to those in need, it is equally crucial to ensure that security risks are adequately addressed. Striking a balance between humanitarian concerns and national security is a complex task that requires careful policy formulation and implementation.
Additionally, immigration policies should address the integration and assimilation of immigrants into the host society. By promoting social cohesion and facilitating the integration of immigrants, countries can reduce the potential for radicalization and social unrest. Effective integration policies contribute to the overall security and well-being of both immigrants and the host community.
C. Strategies to enhance border security
Enhancing border security requires the implementation of various strategies that address the challenges posed by unauthorized entry, smuggling, and other security risks. These strategies aim to strengthen border control and surveillance, improve intelligence gathering and sharing, and enhance cooperation with international partners.
One strategy is the deployment of advanced technology and infrastructure at border checkpoints. This includes the use of biometric systems, surveillance cameras, drones, and other high-tech tools to monitor and detect potential threats. By leveraging technology, countries can enhance their border security capabilities and improve response times.
Another strategy is the development of intelligence-led border security operations. By gathering and analyzing intelligence on potential threats and criminal networks, countries can proactively identify and disrupt illegal activities. Intelligence sharing among law enforcement agencies and international partners is crucial for effective border security.
Cooperation with neighboring countries and international organizations is also essential for enhancing border security. By sharing information, coordinating joint operations, and conducting capacity-building initiatives, countries can collectively address common security challenges. Regional and international collaboration strengthens border security efforts and promotes stability.
Furthermore, investing in the training and professional development of border security personnel is vital. Well-trained and equipped border officers are better prepared to handle security threats and effectively enforce immigration laws. Continuous training and knowledge sharing ensure that border security measures remain up to date and responsive to evolving threats.
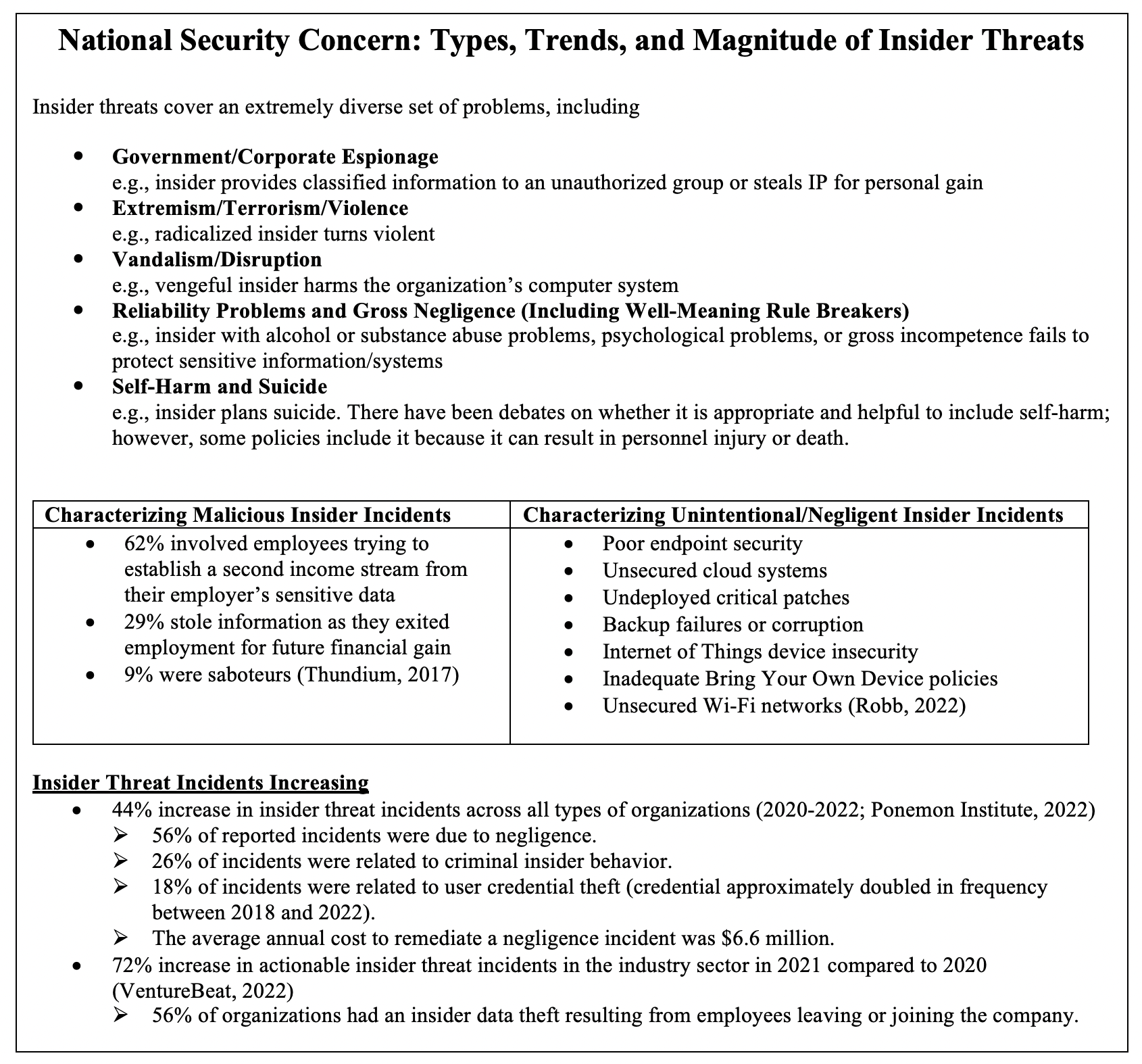
IX. Insider Threats
Insider threats pose a significant risk to organizations, as they involve individuals within the organization who exploit their access and privileges to cause harm. These threats can come from current or former employees, contractors, or business partners who have authorized access to sensitive information and systems. In this section, we will explore the definition and examples of insider threats, analyze vulnerabilities within organizations, and discuss measures to mitigate these threats.
A. Definition and Examples of Insider Threats
Insider threats refer to the potential risks and dangers posed by individuals who have authorized access to an organization’s resources, systems, or data. These individuals may intentionally or unintentionally misuse their access to compromise the confidentiality, integrity, or availability of the organization’s assets.
There are various types of insider threats that organizations should be aware of:
- Malicious Insiders: These individuals intentionally exploit their access for personal gain or to harm the organization. They may steal sensitive data, sabotage systems, or engage in fraudulent activities.
- Negligent Insiders: Negligent insiders pose a threat due to their carelessness or lack of awareness. They may inadvertently disclose sensitive information, fall victim to phishing attacks, or fail to follow security protocols.
- Compromised Insiders: Compromised insiders are individuals whose access credentials have been compromised by external attackers. These attackers may use stolen credentials to gain unauthorized access and carry out malicious activities.
Examples of insider threats include:
- An employee stealing customer data to sell it to a competitor.
- A contractor accidentally sharing sensitive information with unauthorized individuals.
- An employee clicking on a phishing email and unknowingly installing malware on the organization’s network.
- A disgruntled employee sabotaging critical systems before leaving the organization.
B. Analysis of Vulnerabilities within Organizations
Organizations face various vulnerabilities that can be exploited by insider threats. Understanding these vulnerabilities is crucial for implementing effective security measures. Some common vulnerabilities include:
- Lack of Employee Awareness: Insufficient security awareness among employees can make them susceptible to social engineering attacks and phishing attempts.
- Inadequate Access Controls: Weak access controls, such as shared or easily guessable passwords, can allow insiders to gain unauthorized access to sensitive information.
- Insider Privileges: Employees with excessive privileges or access rights may abuse their privileges for personal gain or to carry out malicious activities.
- Poor Monitoring and Detection: Inadequate monitoring and detection mechanisms can make it difficult to identify and respond to insider threats in a timely manner.
C. Measures to Mitigate Insider Threats
Organizations can implement several measures to mitigate the risks posed by insider threats:
- Employee Training and Awareness: Regular security awareness training can educate employees about the risks associated with insider threats and teach them how to identify and report suspicious activities.
- Strong Access Controls: Implementing strong access controls, such as multi-factor authentication and least privilege principles, can limit the potential damage caused by insider threats.
- Continuous Monitoring: Implementing robust monitoring and detection systems can help identify unusual or suspicious activities that may indicate insider threats.
- Regular Auditing and Reviews: Conducting regular audits and reviews of access privileges and user activities can help identify any anomalies or policy violations.
- Incident Response Plan: Having a well-defined incident response plan in place can ensure a swift and effective response to insider threats, minimizing the impact on the organization.
By implementing these measures, organizations can significantly reduce the risks associated with insider threats and protect their sensitive information and systems.
In this section, we will delve into the complex and ever-present issue of biological threats and pandemics. As a content writer with a deep understanding of national security and the potential risks we face, I will provide you with an overview of biological threats, analyze potential pandemics and their impact on national security, and discuss preparedness and response strategies for such threats.
A. Overview of Biological Threats
Biological threats pose a unique and significant risk to national security. These threats can arise from naturally occurring diseases, accidental releases, or deliberate acts of bioterrorism. The potential consequences of a biological threat are far-reaching, with the potential to cause widespread illness, death, and social and economic disruption.
One of the most challenging aspects of biological threats is their unpredictability. Pathogens can mutate, evolve, and spread rapidly, making it difficult to anticipate and control their impact. Furthermore, the ease of travel and globalization has increased the likelihood of infectious diseases spreading across borders, amplifying the potential for a global pandemic.
It is crucial for national security agencies and healthcare systems to have a comprehensive understanding of the various biological threats we face. This includes identifying high-risk pathogens, monitoring disease outbreaks, and developing robust surveillance and early warning systems. By staying vigilant and proactive, we can mitigate the risks posed by biological threats.
B. Analysis of Potential Pandemics and Their Impact on National Security
Pandemics have the potential to cause widespread devastation, both in terms of human lives and national security. The COVID-19 pandemic, which has affected nearly every corner of the globe, serves as a stark reminder of the impact a pandemic can have on our society.
When analyzing potential pandemics, it is essential to consider factors such as the virulence of the pathogen, its transmission rate, and the vulnerability of the population. By understanding these factors, we can assess the potential impact on healthcare systems, economies, and social stability.
Pandemics can strain healthcare systems to their limits, overwhelming hospitals and healthcare workers. This not only leads to a higher mortality rate but also hampers the ability to respond effectively to other national security threats. Additionally, pandemics can disrupt supply chains, weaken economies, and exacerbate social inequalities, further destabilizing nations.
As we analyze potential pandemics and their impact on national security, it is crucial to prioritize preparedness and response strategies. This includes investing in research and development of vaccines and treatments, strengthening healthcare infrastructure, and enhancing international cooperation and coordination. By taking proactive measures, we can minimize the impact of pandemics on national security.
C. Preparedness and Response Strategies for Biological Threats
Preparedness and response strategies are vital in mitigating the risks posed by biological threats. These strategies encompass a range of measures, from prevention and surveillance to rapid response and recovery.
Prevention is a key component of preparedness. This involves implementing robust biosecurity measures, such as strict regulations on the handling and storage of dangerous pathogens, as well as promoting public health initiatives to reduce the spread of infectious diseases.
Surveillance plays a crucial role in early detection and response. By monitoring disease outbreaks and implementing effective surveillance systems, we can identify potential threats and take swift action to contain them. This includes enhancing laboratory capabilities, establishing real-time data sharing mechanisms, and leveraging advanced technologies such as genomic sequencing.
Rapid response is essential in containing and mitigating the impact of biological threats. This requires a coordinated effort between various stakeholders, including government agencies, healthcare systems, and international organizations. By implementing emergency response plans, conducting drills and simulations, and ensuring adequate stockpiles of medical supplies, we can mount an effective response to biological threats.
Recovery is a critical phase in the aftermath of a biological threat or pandemic. This involves rebuilding healthcare systems, restoring economic stability, and addressing the social and psychological impacts on affected communities. By investing in long-term recovery efforts, we can strengthen resilience and better prepare for future biological threats.
